





Published on Jan 09, 2026
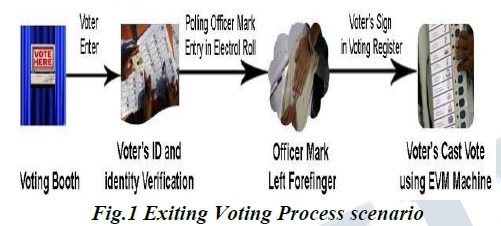
In this paper a new authentication technique in online voting system using facial recognition of the voter is used. In India, currently there are two types of voting system in practice. They are secret Ballet paper and Electronic Voting Machines (EVM), but both of the process have some limitation or demerits. In India online voting has not been yet implemented. The current voting system is not safe and secure too. The voters need to go to distributed places like polling booths and stand in a long queue to cast their vote, because of these reasons most of the people misses their chance of voting. The voter who is not eligible can also cast its vote by fake means which may leads to many problems. That’s why in this project we have to propose a system or way for voting which is very effective or useful in voting. In our approach we have three level of security in voting process.
The first level is the verification of unique id number (UID), second level is the verification of election id number (EID) and third level is face recognition or face matching. The security level of our system is greatly improved by the new application method for each voter. The user authentication process of the system is improved by adding face recognition in an application which will identify whether the particular user is authenticated user or not.
Now a day in India two types of method are used for voting. [1] The first method is secret ballot paper, in which lots of paper are used and [2] second method is EVM (electronic voting machine) which is used since 2003. we have to propose a method or way for online voting that is more secure than the existing system. In this proposed project face detection and recognition concept is used to identify the exact person. There are three levels of verification were used for the voters in our proposed system. The first one is Unique id number verification, second level of verification is election commission id or voter card number, if your election commission id number is correct then you have to go for third level of security which is the main security level where the system recognize the face of the real voter from the current database of face images given by the election commission. If the captured image is matched with the respective image of the voter in the database, then a voter can cast their vote in the election.as you have to know that in existing system is not much more secure because in existing system security level is only voter card so any one can give other person vote with voter card but here we proposed a way for voting which is more secure than existing system.
In the current voting system, [3] the ballet machines where used in which the symbols of various political parties are displayed. When we press the button with the respective party’s (political party) symbol the voting is done. The chance of fake person casting their vote is more in the existing system. The voting person may use the fake voting card and cast his vote, this may cause problem. In the existing system, the person has to travel long places to his constituency to cast his vote. Therefore, we need an effective method to identify the fake voters during voting. So, the process is used for detecting the right person and also making the system to work in online, which will help the voters to cast their vote from their place itself.
In this project we are working with three differentdifferent security levels Level1: -Unique id number (UID) [4]. At the time of voter registration system will request for the unique id from the voter. The entered unique id is verified from the database provide by the election commission. Level2: Election commission id card number. [5] In the second level of verification, the voter has to enter the election commission id or voter’s id number. The entered id number is verified from the database provide by the election commission. Level3: - Face recognition with respective election commission id number. In this level, Eigen face algorithm is used to verify the facial image of the voters from the database provided by the election commission.
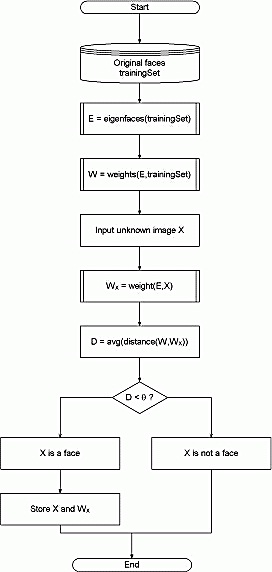
The main concept of Eigen Face algorithm is to follow the appearance –based approach to face recognitio. It is used to capture the variation in a collection of face images and this information is use to encode the particular images of individual faces. Then the encoded images of individual faces are compared with the collection of face images in a holistic manner. The Eigen faces itself form a basis set of all images used to construct the covariance matrix. The formed smaller set of basis images are used to represent the original training images which produces dimension reduction. By comparing how faces are represented by the basis set, the classification can be achieved. Face Images are projected into a feature space (“Face Space”) that best encodes the variation among known face images. The face space is defined by the “eigenfaces”, which are the eigenvectors of the set of faces.
Smart Voting System Support through Face Recognition doesn’t fully show the all the equipment that are to be connected to raspberry pi, but covers all major functional units. The IR frames are connected over mirror but still they work fine because it’s a co-ordinate based touch detection by the IR sensors placed at the side of frames and doesn’t require the frame to be directly having contact with monitor behind mirror. The microphone is connected via sound card on USB port of Pi. The camera can be connected to USB port or the Pi camera can be connected to camera slot on Pi. The 8-channel relay is connected to GPIO pins on Pi for controlling the home appliances. To access the internet the Pi is connected to home Wi-Fi network. The programming of the Pi for displaying the UI on the screen is done using Python, the total description of how coding is implemented is described in Section 3 of the document.
•Initialization: Acquire the training set and calculate Eigen faces (using PCA projections) which define Eigen space.
• When a new face is encountered, calculate its weight.
• Determine if the image is face.
•If yes, classify the weight pattern as known or unknown.
• (Learning) If the same unknown face is seen several times incorporate it into known faces. Principal Component Analysis
•Eigen face follows the Principal Component Analysis approach, in which face space forms a cluster in image space


Data used here are from the ORL database of faces. Facial images of 16 persons each with 10 views are used. - Training set contains 16×7 images.
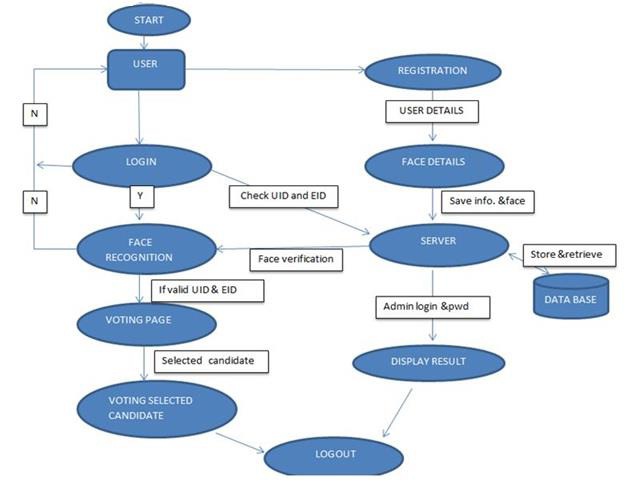
i). Every New User in the India is first register for Voting. So, our first step is registration
ii). At that time of Registration System Capture, the Face of the user by using Web Camera and Store the Face sample in the Server Database for Security Purpose.
iii). At the time of election, we will use three level of security first one is unique id verification second one is voter id verification third one is face recognition.
iv). System will be checking whatever unique id and voter id entered by the voter is correct or not.
v). If unique id or voter id is correct than system will take image of voter and compare with the respective image of database or server.
vi). If the image in database is matching with the captured image of the voter, then he/she is allowed to cast is vote.
vii). On the voting page all the party whatever party contest in the election symbols /buttons will be there. Voter can cast his /her vote in the election.
viii). As soon as voter will give vote the id of voter logout automatically so we can say that a voter can give only one vote.
ix). On counting form only election commission authorized user can login with the secure id and password if both id and password is correct then voting process will be continuing.
As we see that existing voting system has many defects such as lengthy process, time taking, not secure, bogus voting, no security level but now we can say that our approach is more useful and secure from the existing system. Since, we are using three level of security in this proposed system the false voters can be easily identified. The facial authentication technique is very much useful in identifying the fraud voters, so we can avoid the bogus votes during election commission. The voters can cast their voting from anywhere by login to our proposed smart voting system through internet. As every operation is performed through internet connectivity so, it is onetime investment for government. Voters’ location is not important but their voting is important. As data is stored in centralized repository so, data is accessible at any time as well as backup of the data is possible. Smart voting system provides updated result at each and every minute. Also requires less man power and resources. The database needs to be updated every year or before election so that new eligible citizens may be enrolled and those who are dead are removed from the voter list.
1. Pandit, Varad, Prathamesh Majgaonkar, Pratik Meher, Shashank Sapaliga, and Sachin Bojewar. "Intelligent security lock." In Trends in Electronics and Informatics (ICEI), 2017 International Conference on, pp. 713-716. IEEE, 2017.
2. Chauhan, C. U., Abhishek Kalnawat, Akshay Aswale, Ujwal Gautam, and Roshan Nemad. "Survey Paper on a Novel Approach: Web Based Technique for Vote Casting." International Journal of Engineering and Management Research (IJEMR) 7, no. 5 (2017): 71GER, BARRY. "CONTENTIOUS POLITICS AND URBAN DESIGN: TOWARD A NEW ARCHITECTURAL THEORY." International Journal of Architecture and Urban Studies (2017): 18
| Are you interested in this topic.Then mail to us immediately to get the full report.
email :- contactv2@gmail.com |