 |
| ||||||||||||||||||||
|
| |||||||||||||||||||||
Optimal Jamming Attacks and Network Defense Policies in Wireless Sensor Networks
|
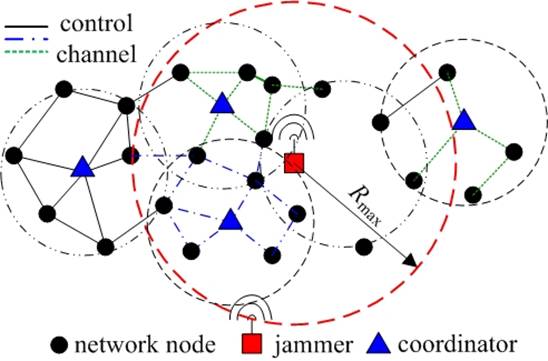
Abstract We consider a scenario where a sophisticated jammer jams an area in a single-channel wireless sensor network. The jammer controls the probability of jamming and transmission range to cause maximal damage to the network in terms of corrupted communication links. The jammer action ceases when it is detected by a monitoring node in the network, and a notification message is transferred out of the jamming region. The jammer is detected at a monitor node by employing an optimal detection test based on the percentage of incurred collisions. On the other hand, the network computes channel access probability in an effort to minimize the jamming detection plus notification time. In order for the jammer to optimize its benefit, it needs to know the network channel access probability and number of neighbors of the monitor node. Accordingly, the network needs to know the jamming probability of the jammer. We study the idealized case of perfect knowledge by both the jammer and the network about the strategy of one another, and the case where the jammer or the network lacks this knowledge. The latter is captured by formulating and solving optimization problems, the solutions of which constitute best responses of the attacker or the network to the worst-case strategy of each other. We also take into account potential energy constraints of the jammer and the network. We extend the problem to the case of multiple observers and adaptable jamming transmission range and propose a intuitive heuristic jamming strategy for that case. Proposed System Multi-channel wireless networks utilize several orthogonal frequency bands to eliminate interference between parallel transmissions and hence, improve the network capacity. Due to their increased performance compared to single-channel networks, they are being integrated into various network architectures, such as mobile ad hoc, vehicular, sensor, wireless local area, mesh, and cognitive radio networks. The increased capacity of multi-channel networks can be translated into actual throughput only if critical network functions such as channel allocation and routing are efficiently coordinated. These functions are collaboratively coordinated by exchanging messages on a broadcast channel known as the control channel. From a security point of view, convergence on a pre-assigned control channel constitutes a single point of failure. An adversary can severely degrade the network performance by launching a Denial of Service (DoS) attack on the control channel, thus negating any gain due to the availability of multiple data channels. A sophisticated adversary can intelligently utilize jamming to attack higher-layer functionalities and deny network availability at a very small energy cost. Module Description:
Hardware Requirements:
S/W System Configuration:-
<< back
|
Related Projects : File Security System ,M-banking ,Flaw Tracking System ,Fleet Manager ,Friend Mapper on Mobiles ,Global Tracker ,Good Welfare Services ,Health Maintenance System ,Image Compression and De-compression ,Image Processing Editor ,Improving Utilization Of Infrastructure Clouds , Information Content-Based Sensor Selection ,Information Portal ,Insurance Broker System ,Learning Made Easy , Light-Weight Multi-Document Summarization Based On Two-Pass Re Ranking ,Load Shedding In Mobile Systems With Mobiqual ,M-banking ,MACA ,Mailing Portal ,Mail Client ,Marine Operations And Management System ,Medical Image Compression ,Millennium Planning ,Mindtech Bug And Component Systems ,Minimum Bandwidth Reservations For Periodic Streams In Wireless Real Time Systems ,Mitigation of Control Channel Jamming ,Mobi-Thesaurus ,Mobile Advertisement System ,Mobile Banking System
| Copyright © V2computers 2006 through 2017 |