





Published on Feb 14, 2025
Slammer (sometimes called Sapphire) was the fastest computer worm in history. As it began spreading throughout the Internet, the worm infected more than 90 percent of vulnerable hosts within 10 minutes, causing significant disruption to financial, transportation, and government institutions and precluding any human-based response.
In this seminar, I wish to describe how it achieved its rapid growth, dissect portions of the worm to study some of its flaws, and look at the defensive effectiveness against it and its successors.
Slammer began to infect hosts on Saturday, 25 January 2003 , by exploiting buffer-overflow vulnerability in computers on the Internet running Microsoft's SQL Server or Microsoft SQL Server Desktop Engine (MSDE) 2000. David Litchfield of Next Generation Security Software discovered this underlying indexing service weakness in July 2002; Microsoft released a patch for the vulnerability before the vulnerability was publicly disclosed. Exploiting this vulnerability, the worm infected at least 75,000 hosts, perhaps considerably more, and caused network outages and unforeseen consequences such as canceled airline flights, interference with elections, and ATM failures
The worm's spreading strategy uses random scanning--it randomly selects IP addresses, eventually finding and infecting all susceptible hosts. Random-scanning worms initially spread exponentially, but their rapid new-host infection slows as the worms continually retry infected or immune addresses. Thus, as with the Code Red worm shown in Figure 2, Slammer's infected-host proportion follows a classic logistic form of initial exponential growth in a finite system. We label this growth behavior a random constant spread (RCS) model.
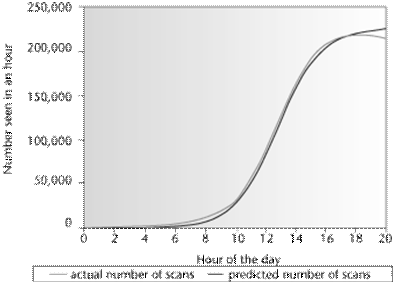
Slammer's spread initially conformed to the RCS model, but in the later stages it began to saturate networks with its scans, and bandwidth consumption and network outages caused site-specific variations in its observed spread. Figure 3 shows a data set from the Distributed Intrusion Detection System project (Dshield) compared to an RCS model. The model fits extremely well up to a point where the probe rate abruptly levels out.
Bandwidth saturation and network failure (some networks shut down under the extreme load) produced this change in the probe's growth rate.
While Slammer spread nearly two orders of magnitude faster than Code Red, it probably infected fewer machines. Both worms use the same basic scanning strategy to find vulnerable machines and transfer their exploitive payloads; however, they differ in their scanning constraints. While Code Red is latency-limited, Slammer is bandwidth-limited, enabling Slammer to scan as fast as a compromised computer can transmit packets or a network can deliver them. Slammer's 376 bytes comprise a simple, fast scanner. With its requisite headers, the payload becomes a single 404-byte user datagram protocol (UDP) packet. Contrast Slammer's 404 bytes with Code Red's 4 Kbytes or Nimda's 60 Kbytes
| Are you interested in this topic.Then mail to us immediately to get the full report.
email :- contactv2@gmail.com |