




Published on Nov 30, 2023
ATM (Automated Teller Machine) is an electronic telecommunication device that is used to perform financial transaction without need for human clerk or bank teller. ATMs extend traditional banking hours by dispensing cash and making other transaction available 24 hours a day. In ATM machines, the user is identified by inserting an ATM card and authentication is provided by the customer entering a PIN. The PIN provided to the customer is compared with recorded reference PIN number in the bank server. In the existing system, the user has to insert the card and the PIN number. If the PIN is correct, the system allows for the transaction. Otherwise, the system asks for the PIN again and it allows maximum of three times to enter it. After 3 trials the ATM card will get blocked. To reactivate the card user need to visit the bank and do the bank formalities, which is tedious and time consuming job.
Biometrics is the science of establishing the identity of an individual based on physical, chemical or behavioral attributes of a person. Fingerprint is a pattern of ridges and valleys on the surface of a fingertip. It often used for biometric identification. Fingerprints are detailed, nearly unique, difficult to alter and durable over the life of an individual. To reactivate that ATM card in the ATM center itself we are using fingerprint biometric.
Keywords: - Fingerprint; ATM; PIN; Harris corner detection algorithm; SURF algorithm
PIN based verification is mostly done in the automatic teller machine transactions. Enhancing this security, user authentication process is an important activity. The major problems include shoulder-surfing attacks, replay attacks, card cloning, and PIN sharing. Multiple researches have also been conducted to create systems supporting card-less transactions. These are getting popular, where users can use additional personal devices, such as mobiles phones, to perform atm transactions. Shoulder-surfing attacks, also known as observation attacks, are most common threat for ATM authentication.
In this case, the attacker simply views the entry procedure of the PIN by the authorized user to get hold of the secret information. Credit card and debit card frauds due to identity thefts are increasing every year. Additionally, there are scamming techniques using fake terminals, credit card cloning, and remote relay which make the process of user protection harder. The attacker can be standing in queue behind the authenticating person and looking at the PIN entry and execute a shoulder-surfing or observation attack. The attacker may also install a small camera on the top surface of the ATM terminal to record PIN entries of users at the point-of-service.
The attacker can install a card skimming device on the ATM machine to get hold of the user’s card information. Such devices fit at the card slot on ATM machines and record the card information as the user slides in their card. The security level is thus improved by providing a PIN authentication protocol for ATM using mobile applications in smart phones. Image processing technique is further used for user identity checking process when a maximum of three PIN attempts is made by the user.
Usually the user inserts the ATM card in the ATM machine and enters Personal Identification Number (PIN) for the transactions. If the user forgets the PIN and enters the wrong PIN then the ATM machine will provide two more attempts to enter the valid PIN. If the user fails to provide the correct PIN after three attempts, the bank server will block the ATM card of the user. Now user has to visit the bank to reactivate his/her ATM card, which is time consuming
1) To avoid the user to visit the bank and do the formalities to reactivate his/her ATM card.
2) To activate the ATM card of the user at the ATM centre itself with the help of finger print of the user.
3) To alert owner of the ATM card in case of misuse.
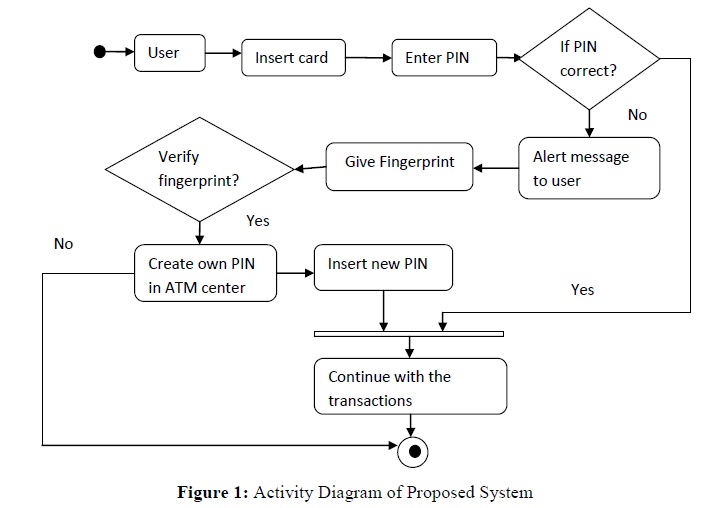
The proposed methodology is based on identification of fingerprint of the ATM user. The user inserts the ATM card and enters PIN to perform transactions. If the user enters the invalid PIN for three times, an alert message will be sent to registered mobile number and also a pop-up window will open on the ATM machine. The pop-up window displays the message “You have entered wrong PIN; please give your registered fingerprint to create new PIN”. User provides the finger impression for authentication. If fingerprint matches then the bank server will provide flexibility for the user to create his/her new PIN on the ATM machine itself. After that user will get message that you have successfully got new PIN. Now user can continue transactions with this new PIN as earlier. Figure 1 shows the activity diagram of proposed system.
Input: Image of fingerprint.
Output: Detection of key points.
1. Input image is converted into greyscale image then it is converted into binary image.
2. Skeleton image is obtained.
3. Using Harris corner detection algorithm, key points of fingerprint are detected.
4. Using key points, the fingerprints are matched.
The Matching Algorithm plays a key role in fingerprint recognition steps. We are using matching algorithms and they are SURF (Speeded-Up Robust Features) algorithm and Harris corner detection algorithm.
RAM: 4GB
Fingerprint scanner with USB cable
Processor: Intel core-i5, 64-bit
OS: Windows 7 & above
Back-end: Python
Front-end: Java
The proposed ATM security system provides a mechanism for recovery of ATM PIN by using fingerprint identification. The developed system is able to authenticate the user based on fingerprint identification. The system is able to send an alert message to ATM card owner for entering the wrong PIN. The alert message is also sent to the owner of the card upon successful creation of new PIN.
From the tests carried out we have been able to prove that, the biometric identification for ATM transactions can be practically implemented in a real time environment. The developed system provides ATM users with the facility to change the PIN in the ATM machine itself.
Bank can provide helpline number to block the ATM card. In case if the ATM card is being misused, user will get the message of transaction which is performed through his/her card. By referring that message, user can call to helpline number to block the ATM card through the registered mobile number.
ATM authentication using PIN-based entry is highly susceptible to shoulder- surfing or observation attacks. In this system, we propose the Secure-PIN- Authentication, OTP-based authentication service for ATMs using Mobile devices. The protocol does not require any additional hardware support for currently operating ATM machine terminals and employs offloaded computation from the mobile device for verifying the transaction requests.
1. Alhassan M.E,Ganiyur S.O,Muhammad-Bello B.L,” An enhanced ATM security system using second level authentication”,International journal of computer application(0975-8887),vol 111-no 5,feb 2015.
2. A.Gera,N.sethi, “A revived survey of various credit card fraud detection techniques,” International Journal of Computer Science and Mobile Computing, vol. 3, no. 4, pp. 780 – 791, April 2014
3. G. Stanley, “Card-less financial transaction,” Apr. 21 2014, US Patent App. 14/257,588.
4. Gajjala Askok,Sai Venupradhap, Sivakumar, “Design and Implementation of security based ATM theft Monitoring System”, International Journal of Engineering Inventions , vol 3,2013