





Published on Feb 14, 2025
Bluetooth wireless technology is a short-range communications technology intended to replace the cables connecting portable and/or fixed devices while maintaining high levels of security.
The key features of Bluetooth technology are robustness, low power, and low cost. The Bluetooth specification defines a uniform structure for a wide range of devices to connect and communicate with each other. Bluetooth technology has achieved global acceptance such that any Bluetooth enabled device, almost everywhere in the world, can connect to other Bluetooth enabled devices in proximity. Bluetooth enabled electronic devices connect and communicate wirelessly through short-range, ad hoc networks known as piconets. Each device can simultaneously communicate with up to seven other devices within a single piconet. Each device can also belong to several piconets simultaneously. Piconets are established dynamically and automatically as Bluetooth enabled devices enter and leave radio proximity.
Most Bluetooth devices are described as 'Class 2'. These are very low power (typically 1 milliwatt - 1/1000th of a watt) and have a range of about 10 m (33 ft).Some devices - for example, some plug in'dongles' that can be added to to laptop computers - are Class 1. These have range comparable to that of Wi-Fi, ie, 100 m or 330 ft. With Bluetooth, short range is actually a benefit, because it reduces the chance of interference between your Bluetooth devices and those belonging to other people nearby.
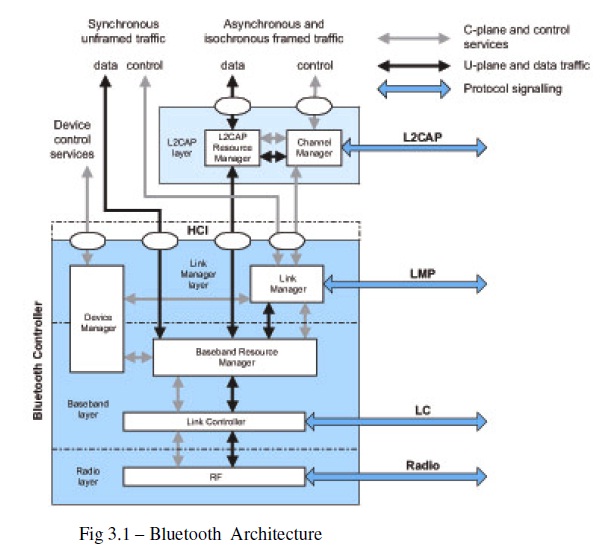
Above the physical channel there is a layering of links and channels and associated control protocols. The hierarchy of channels and links from the physical channel upwards is physical channel, physical link, logical transport, logical link and L2CAP channel.
Within a physical channel, a physical link is formed between any two devices that transmit packets in either direction between them. In a piconet physical channel there are restrictions on which devices may form a physical link. There is a physical link between each slave and the master. Physical links are not formed directly between the slaves in a piconet.
The physical link is used as a transport for one or more logical links that support unicast synchronous, asynchronous and isochronous traffic, and broadcast traffic. Traffic on logical links is multiplexed onto the physical link by occupying slots assigned by a scheduling function in the resource manager.
A control protocol for the baseband and physical layers is carried over logical links in addition to user data. This is the link manager protocol (LMP). Devices that are active in a piconet have a default asynchronous connection-oriented logical transport that is used to transport the LMP protocol signaling. For historical reasons this is known as the ACL logical transport. The default ACL logical transport is the one that is created whenever a device joins a piconet. Additional logical transports may be created to transport synchronous data streams when this is required. The link manager function uses LMP to control the operation of devices in the piconet and provide services to manage the lower architectural layers (radio layer and baseband layer). The LMP protocol is only carried on the default ACL logical transport and the default broadcast logical transport.
Above the baseband layer the L2CAP layer provides a channel-based abstraction to applications and services. It carries out segmentation and reassembly of application data and multiplexing and de-multiplexing of multiple channels over a shared logical link. L2CAP has a protocol control channel that is carried over the default ACL logical transport. Application data submitted to the L2CAP protocol may be carried on any logical link that supports the L2CAP protocol.
This section describes the function and responsibility of each of the blocks
Several new features are introduced in Bluetooth Core Specification 2.1 +EDR. The major areas of improvement are:
• Erroneous Data Reporting
• Encryption Pause and Resume
• Extended Inquiry Response
• Link Supervision Timeout Changed Event
• Non-Automatically-Flushable Packet Boundary Flag
• Secure Simple Pairing
• Sniff Subrating
• Security Mode 4
The Erroneous Data Reporting configuration parameter shall be used for SCO and eSCO connections only. This parameter determines if the Controller is required to provide data to the Host for every (e)SCO interval, with the Packet Status Flag in HCI Synchronous Data Packets set according to demand.
The Encryption Key Refresh Complete event is used to indicate to the Host that the encryption key was refreshed on the given Connection Handle any time encryption is paused and then resumed. The Controller shall send this event when the encryption key has been refreshed due to encryption being started or resumed If the Encryption Key Refresh Complete event was generated due to an encryption pause and resume operation embedded within a change connection link key procedure, the Encryption Key Refresh Complete event shall be sent prior to the Change Connection Link Key Complete event.If the Encryption Key Refresh Complete event was generated due to an encryption pause and resume operation embedded within a role switch procedure,the Encryption Key Refresh Complete event shall be sent prior to the Role Change event.
The Extended Inquiry Response provides information about the local device in response to inquiry from remote devices. The configuration parameter has two parts, a significant part followed by a non-significant part. The non-significant part contains only zero octets. The length of the extended inquiry response configuration parameter is 240 octets.
The Link Supervision Timeout Changed event is used to notify the slave's Host when the Link Supervision Timeout parameter is changed in the slave Controller. This event shall only be sent to the Host by the slave controller upon receiving an LMP supervision timeout PDU from the master.
Sniff subrating provides a mechanism for further reducing the active duty cycle ,thereby enhancing the power-saving capability of sniff mode. Sniff subrating allows a Host to create a guaranteed access-like connection by specifying maximum transmit and receive latencies. This allows the basebands to optimize the low power performance without having to exit and re-enter sniff mode using Link Manager commands .
A Bluetooth device in security mode 4 shall classify the security requirements of its services using at least the following attributes (in order of decreasing security):
Authenticated link key required
Unauthenticated link key required
No security required
An authenticated link key is a link key where either the numeric comparison ,out-ofband or passkey entry simple pairing association models were used. An authenticated link key has protection against man-in-the-middle (MITM) attacks. To ensure that an authenticated link key is created during the Simple Pairing procedure, the Authentication Requirements parameter should be set to one of the MITM Protection Required options. An unauthenticated link key is a link key where the just works Secure Simple Pairing association model was used. An unauthenticated link key does not have protection against MITM attacks.
When both devices support Secure Simple Pairing, GAP shall default to requiring an unauthenticated link key and enabling encryption. A profile or protocol may define services that require more security (e.g. an authenticated link key)or no security. To allow an unauthenticated link key to be created during the Simple Pairing procedure, the Authentication Requirements parameter may be set to one of the MITM Protection Not Required options. When the device is in Bondable Mode, it shall enable Secure Simple Pairing mode prior to entering Connectable Mode or establishing a link .
A Bluetooth device in security mode 4 shall respond to authentication requests during link establishment when the remote device is in security mode 3 for backwards compatibility reasons. A Bluetooth device in security mode 4 enforces its security requirements before it attempts to access services offered by a remote device and before it grants access to services it offers to remote devices.
Bluetooth has become a revelation in the field of mobile phones. Almost all mobile companies are launching their new models incorporating a Bluetooth device. It has also become an inextricable tool in the field of networking as it provides superior security. It is used for data transfer, lan access, internet bridge, synchronization and are included in several headsets. Vast researches are done in the field of Bluetooth. Bluetooth special interest group are planning to incorporate Ultra Wide Band Radio Technology into Bluetooth which will enable very fast data transfer rates for Bluetooth devices. They are also planning to build low energy and ultra small version to incorporate Bluetooth devices in wrist watches. The day wont be far when every mobiles, pc’s, watches will contain a Bluetooth device integrated in it.
1. BLUETOOTH CORE SPECIFICATION v2.1+EDR
2. BLUETOOTH PROTOCOL ARCHITECTURE v1.0
3. https://www.bluetooth.com/Bluetooth/Technology/
4. https://en.wikipedia.org/wiki/Bluetooth
5. https://electronics.howstuffworks.com/bluetooth.htm
| Are you interested in this topic.Then mail to us immediately to get the full report.
email :- contactv2@gmail.com |