




Published on Apr 02, 2024
Wireless local area networks (WLANs) based on the Wi-Fi (wireless fidelity) standards are one of today's fastest growing technologies in businesses, schools, and homes, for good reasons. They provide mobile access to the Internet and to enterprise networks so users can remain connected away from their desks. These networks can be up and running quickly when there is no available wired Ethernet infrastructure.
They can be made to work with a minimum of effort without relying on specialized corporate installers. Some of the business advantages of WLANs include:
" Mobile workers can be continuously connected to their crucial applications and data;
" New applications based on continuous mobile connectivity can be deployed;
" Intermittently mobile workers can be more productive if they have continuous access to email, instant messaging, and other applications;
" Impromptu interconnections among arbitrary numbers of participants become possible.
" But having provided these attractive benefits, most existing WLANs have not effectively addressed security-related issues.
All wireless computer systems face security threats that can compromise its systems and services. Unlike the wired network, the intruder does not need physical access in order to pose the following security threats: Eavesdropping
This involves attacks against the confidentiality of the data that is being transmitted across the network. In the wireless network, eavesdropping is the most significant threat because the attacker can intercept the transmission over the air from a distance away from the premise of the company.
The attacker can modify the content of the intercepted packets from the wireless network and this results in a loss of data integrity.
The attacker could gain access to privileged data and resources in the network by assuming the identity of a valid user. This kind of attack is known as spoofing. To overcome this attack, proper authentication and access control mechanisms need to be put up in the wireless network.
In this attack, the intruder floods the network with either valid or invalid messages affecting the availability of the network resources. The attacker could also flood a receiving wireless station thereby forcing to use up its valuable battery power.
The other threats come from the weakness in the network administration and vulnerabilities of the wireless LAN standards, e.g. the vulnerabilities of the Wired Equivalent Privacy (WEP), which is supported in the IEEE 802.11 wireless LAN standard.
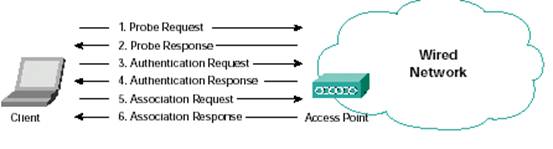
Authentication in the 802.11 specification is based on authenticating a wireless station or device instead of authenticating a user. The specification provides for two modes of authentication: open authentication and shared key authentication. The 802.11 client authentication process consists of the following transactions:
• Client broadcasts a probe request frame on every channel
• Access points within range respond with a probe response frame
• The client decides which access point (AP) is the best for access and sends an authentication request
• The access point will send an authentication reply
• Upon successful authentication, the client will send an association request frame to the access point
• The access point will reply with an association response
• The client is now able to pass traffic to the access point
As network security becomes increasingly critical to securing business transactions, businesses must integrate security into the network design and infrastructure itself. Security policy enforcement is most effective when it is an inherent component of the network.
The Cisco IOS Firewall is a security-specific option for Cisco IOS Software. It integrates robust firewall functionality and intrusion detection for every network perimeter. It adds greater depth and flexibility to existing Cisco IOS security solutions (i.e., authentication, encryption, and failover), by delivering state-of-the-art security features: stateful, application-based filtering; dynamic per-user authentication and authorization; URL Filtering and others. When combined with Cisco IOS IPSec and Cisco IOS Technologies such as L2TP tunneling and Quality of Service (QoS), Cisco IOS Firewall provides a complete, integrated virtual private network (VPN) solution.
Cisco IOS Firewall is available on a wide range of Cisco IOS Software releases. It offers sophisticated security and policy enforcement for connections within an organization (intranet) and between partner networks (extranets), as well as for securing Internet connectivity for remote and branch offices.The Cisco IOS Firewall is the best choice for integrating multiprotocol routing with security policy enforcement and enabling managers to configure a Cisco router as a firewall. It scales to allow customers to choose a router platform based on bandwidth, LAN/WAN density, and multiservice requirements; simultaneously, it benefits from advanced security.
The Cisco IOS Firewall interoperates seamlessly with Cisco IOS Software, providing outstanding value and benefits:
Installed on a Cisco router, Cisco IOS Firewall is an all-in-one, scalable solution that performs multiprotocol routing, perimeter security, intrusion detection, VPN functionality, and per-user authentication and authorization.
Integrating firewall functionality into a multiprotocol router leverages an existing router investment, without the cost and learning curve associated with a new platform.
Deploying Cisco IOS Firewall with Cisco IOS encryption and QoS VPN features enables secure, low-cost transmissions over public networks. It ensures that mission-critical application traffic receives high-priority delivery.
Cisco IOS Firewall is available for a wide variety of router platforms. It scales to meet the bandwidth and performance requirements of any network.
Combining the Cisco IE2100 and the Cisco IOS XML application enables a network administrator to drop ship any Cisco router with little or no pre-configuration to a given destination. The router pulls the most current Cisco IOS Software release router configuration and its security policy configuration for the Firewall when it is connected to the Internet.
Cisco IOS Firewall is supported on a majority of Cisco routers platforms, thus delivering important benefits that include multiservice integration (data/voice/video/dial), advanced security for dialup connections. On the Cisco 7100, 7200 and 7400 Series Routers, additional benefits include integrated routing and security at the Internet gateway for large enterprises and service provider customer premise equipment (CPE).
| Are you interested in this topic.Then mail to us immediately to get the full report.
email :- contactv2@gmail.com |