





Published on Feb 14, 2025
The 'Enhancing LAN Using Cryptography And Other Modules' suggests important ways to remove the shortcomings of the present network management systems. It allows the administrator to gain more control over remote machine on the network.
The network is used to its full potential. The proposed system is implemented in .net. It has the following modules. Each of the modules addresses some key feature of the network. Modules includes process management , monitoring ,desktop capturing ,remote processing ,file transfer ,chatting, wakeon lan and a GPS receive r for user system management. Our project have the following advantages over existing systems.
• Security of data : Protection of data during their transmission over a collection of interconnected network by using cryptography.
• Faster and Better Communication- When our requirement is to communicate with any of the colleagues sitting in the same organization and not with any of the personal friends then why to communicate over the congested network of thousands of computers called Internet instead of exploiting the features of high speed Local Area Network which already exists in almost all enterprises and institutions.
• Timely and Assured Transfers- For tasks such as general notifications the broadcasting feature is hundred times faster than a peon circulating the notices to all employees. Networks are not just for data transfers anymore. Data transfer can be used in the following, not only interesting but also productive ways.
System management- Here we use the GPS receiver for time synchronization through which the administrator can shut down the user system.
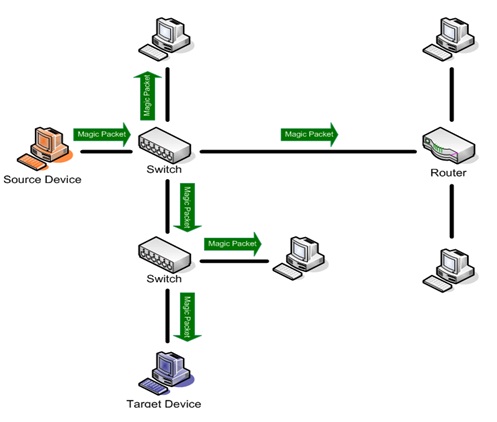
Wake on LAN is implemented using a special network message called a magic packet.The magic packet contains the MAC address of the destination computer.The listening computer waits for a magic packet addressed to it and then initiates system wake up.The magic packet is sent on the data link layer or layer 2 in the OSI model and broadcast to all NICs using the network broadcast address;the IP address is not used.
This is why Wake on LAN is platform independent.Any application,on any platform,can wake up computers running on any other platform. It is a common misconception that because Wake on LAN is built upon broadcast technology it can only be used within the current network subnet.While this is generally the case there are some exceptions inorder for wake on LAN to work,parts of the network interface need to stay on.This consumes standby power,much less than normal operating power.
If wake on Lan is not needed,disabling it may reduce power consumption slightly while the computer is switched off but still plugged in. By using this module, administrator can wakeup the system that is shutdowned by the user.WakeOnLan discovers all other computers in LAN,and enables the admin to wake them.
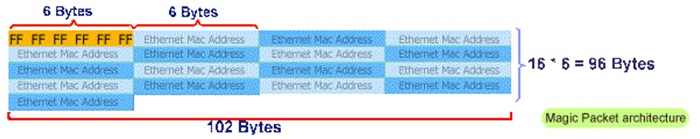
The magic packet is a broadcast frame containing anywhere within its payload 6 bytes of all 255 (FF FF FF FF FF FF in hexadecimal),followed by sixteen repetitions of the target computer's 48-bit MAC address.Since the magic packet is only scanned for the string above and not actually parsed by a full protocol stack,it may be sent as any network and transport layer protocol,although it is typically sent as a UDP datagram to port 7 or 9,or directly over Ethernet.
A standard magic packet has the following basic limitations:
• Requires destination computer MAC address(also may require a SecureOn password)
• Does not provide a delivery confirmation
• May not work outside of the local network
• Requires hardware support of wake on LAN on destination computer
The wake on LAN implementation is designed to be very simple and to be quickly processed by the circuitry present on the Network Interface Card(NIC) with minimal power requirement.Because wake on LAN operates below the protocol layer the MAC address is required and makes IP addresses and DNS names meaningless
The administrator can have complete control over all activity done by his subordinates. By encryption of data/ files security can be enhanced. User system can be managed by admin even if it is shutdown. We can use satellite timing system and to develop an network application (both client and server) that can be used to synchronize the system time of client computers connected to the network with the GPS time.
1. www.ntp-time-server.com
2. www.edu-observatory.org/gps
3. https://en.wikipedia.org/wiki/Wake-on-LAN
4. https://www.codeproject.com/KB/IP/WOL.aspx
5. https://en.wikipedia.org/wiki/Data_Encryption_Standard
| Are you interested in this topic.Then mail to us immediately to get the full report.
email :- contactv2@gmail.com |