




Published on Apr 02, 2024
Wireless local area networks (WLANs) based on the Wi-Fi (wireless fidelity) standards are one of today's fastest growing technologies in businesses, schools, and homes, for good reasons. They provide mobile access to the Internet and to enterprise networks so users can remain connected away from their desks. These networks can be up and running quickly when there is no available wired Ethernet infrastructure.
They can be made to work with a minimum of effort without relying on specialized corporate installers. Some of the business advantages of WLANs include:
" Mobile workers can be continuously connected to their crucial applications and data;
" New applications based on continuous mobile connectivity can be deployed;
" Intermittently mobile workers can be more productive if they have continuous access to email, instant messaging, and other applications;
" Impromptu interconnections among arbitrary numbers of participants become possible.
" But having provided these attractive benefits, most existing WLANs have not effectively addressed security-related issues.
All wireless computer systems face security threats that can compromise its systems and services. Unlike the wired network, the intruder does not need physical access in order to pose the following security threats: Eavesdropping
This involves attacks against the confidentiality of the data that is being transmitted across the network. In the wireless network, eavesdropping is the most significant threat because the attacker can intercept the transmission over the air from a distance away from the premise of the company.
The attacker can modify the content of the intercepted packets from the wireless network and this results in a loss of data integrity.
The attacker could gain access to privileged data and resources in the network by assuming the identity of a valid user. This kind of attack is known as spoofing. To overcome this attack, proper authentication and access control mechanisms need to be put up in the wireless network.
In this attack, the intruder floods the network with either valid or invalid messages affecting the availability of the network resources. The attacker could also flood a receiving wireless station thereby forcing to use up its valuable battery power.
The other threats come from the weakness in the network administration and vulnerabilities of the wireless LAN standards, e.g. the vulnerabilities of the Wired Equivalent Privacy (WEP), which is supported in the IEEE 802.11 wireless LAN standard.
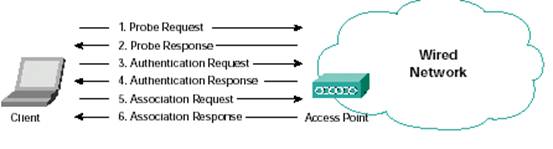
Authentication in the 802.11 specification is based on authenticating a wireless station or device instead of authenticating a user. The specification provides for two modes of authentication: open authentication and shared key authentication. The 802.11 client authentication process consists of the following transactions:
• Client broadcasts a probe request frame on every channel
• Access points within range respond with a probe response frame
• The client decides which access point (AP) is the best for access and sends an authentication request
• The access point will send an authentication reply
• Upon successful authentication, the client will send an association request frame to the access point
• The access point will reply with an association response
• The client is now able to pass traffic to the access point
The SSID is advertised in plain-text in the access point beacon messages. Although beacon messages are transparent to users, an eavesdropper can easily determine the SSID with the use of an 802.11 wireless LAN packet analyzer, like Sniffer Pro. Some access-point vendors, including Cisco, offer the option to disable SSID broadcasts in the beacon messages. The SSID can still be determined by sniffing the probe response frames from an access point. The SSID is not designed, nor intended for use, as a security mechanism. In addition, disabling SSID broadcasts might have adverse effects on Wi-Fi interoperability for mixed-client deployments. Therefore, it is not recommended using the SSID as a mode of security.
Open authentication provides no way for the access point to determine whether a client is valid. This is a major security vulnerability if WEP encryption is not implemented in a wireless LAN. Cisco does not recommend deploying wireless LANs without WEP encryption. In scenarios in which WEP encryption is not needed or is not feasible to deploy, such as public wireless LAN deployments strong, higher-layer authentication can be provided by implementing a Service Selection Gateway (SSG).
Shared key authentication requires the client use a preshared WEP key to encrypt challenge text sent from the access point. The access point authenticates the client by decrypting the shared key response and validating that the challenge text is the same. The process of exchanging the challenge text occurs over the wireless link and is vulnerable to a man-in-the-middle attack. An eavesdropper can capture both the plain-text challenge text and the cipher-text response. WEP encryption is done by performing an exclusive OR (XOR) function on the plain-text with the key stream to produce the cipher-text. It is important to note that if the XOR function is performed on the plain-text and cipher-text are XORed, the result is the key stream. Therefore, an eavesdropper can easily derive the key stream just by sniffing the shared key authentication process with a protocol analyzer.
MAC addresses are sent in the clear as required by the 802.11 specification. As a result, in wireless LANs that use MAC authentication, a network attacker might be able to subvert the MAC authentication process by “spoofing” a valid MAC address. MAC address spoofing is possible in 802.11 network interface cards (NICs) that allow the universally administered address (UAA) to be overwritten with a locally administered address (LAA). A network attacker can use a protocol analyzer to determine a valid MAC address in the business support system (BSS) and an LAA-compliant NIC with which to spoof the valid MAC address.
The most direct way to extend the services of an outside-the-firewall WLAN to internal users is to employ a VPN. A VPN (Virtual Private Network) is an encrypted link into the internal network that runs over a public network, such as the open WLAN we have been describing. Accessing the VPN requires authentication, which can be gauged to the necessary degree of security. For non-critical facilities, a simple ID/password logon may be sufficient. Best practices for remote access security suggest deploying smart cards or tokens to raise the degree of protection. These techniques may be combined with biometric readers or other more esoteric systems for the most critical networks. Practically speaking, VPNs require software on the client and on a VPN server inside the network.
VPNs operate at Layer 3, the network layer of the ISO networking model, so a client needs an IP address and IP connectivity in order to log in to the network. An 802.1X system can kick off the authentication process without previously established IP connectivity. This capacity can also simplify deployment.
One of the advantages of an 802.1X authentication system compared to a VPN is that the wireless network need not be located outside the firewall. Because the access points won’t forward any data aside from the authentication process itself, there is next-to-no opportunity for wireless attackers to access the wired network, even if they can receive the wireless signals in the parking lot. However, this fact is not an argument for deploying wireless networks without solid encryption. Those parking lot intruders could still observe unencrypted wireless traffic and capture e-mail messages, passwords, and any other sensitive data that traverses the wireless network. An 802.1X authentication system will sometimes be easier to deploy than a VPN is if users sometimes need access at different sites. With VPNs, users may need different passwords or smart cards away from their home sites, while 802.1X can simplify multi-site logins.
Radio signals are useful for networking precisely because they radiate out from an antenna into the surrounding space, there is always a potential for data on the WLAN to be visible to a sufficiently sensitive receiver in an unexpected place outside the physical control of the network operators. Any data transiting the network—file transfers, mail, application transactions, Web browsing, instant messaging, music downloading, videoconferences, VoIP phone calls, and much more—is subject to being observed, copied, or conceivably, modified and re-injected onto the network.
The original privacy and integrity mechanism developed and deployed by the WLAN industry was WEP, for Wired Equivalent Privacy. WEP is primarily an encryption algorithm. When it is turned on, it encrypts the data payload of each frame that traverses the network. WEP also supports a form of data integrity checking by calculating a checksum for the encrypted data, appending the checksum to the data payload prior to the encryption operation. After the frame is received and decrypted, the checksum is recalculated and compared to the received checksum. If there is a match, the frame is accepted; if the checksums don’t match, the frame is rejected or otherwise flagged.
The first version of WEP used 40-bit shared secrets, partly because of the then-current export limits on strong encryption and partly to minimize the processing burden. The primary difference between WEP 1 and WEP 2 was the step up to 104-bit secret keys. As processing power has gotten cheaper, breaking 40-bit keys by brute force has become nearly trivial. Pure 104-bit keys are still beyond the capabilities of brute force attacks.
Wi-Fi Protected Access (WPA) is the Wi-Fi Alliance response to the shortcomings of earlier encryption, integrity, and authentication mechanisms. It is a subset of the forthcoming 802.11i wireless security standard. In fact, it makes up the parts of 802.11i that existing products will be able to upgrade to without replacing any hardware. The part of 802.11i that will only be possible with a hardware upgrade is the new Advanced Encryption Standard (AES) encryption algorithm.
| Are you interested in this topic.Then mail to us immediately to get the full report.
email :- contactv2@gmail.com |