




Published on Feb 14, 2025
As information technology evolves over time, the need for a better, faster, more convenient and secure electronic voting is relevant since the traditional election procedures cannot satisfy all of voter’s demands. To increase the number of voters and to offer an enhanced procedure in an election, many researchers have been introducing novel and advanced approaches to secure electronic voting systems.
This paper proposes a secure electronic voting system that provides enhanced security by implementing cryptography and steganography in Java. As a preliminary investigation, two steganography techniques are considered and their performances are compared for different image file formats.
Voting has played a major role in the democratic societies. Traditional voting procedure uses paper-based ballot. However, this approach is costly, inconvenient and time consuming for voters. Many people nowadays prefer a more instant way to vote. With the evolution of computer technology, many researchers are proposing secure, reliable and convenient electronic voting systems as a substitute to the traditional voting procedure. It thus helps to encourage each voter to make use of their right to vote. Such systems have to be designed to satisfy the following requirements.
• Completeness – All valid votes are counted correctly.
• Soundness – The dishonest voter cannot disrupt the voting.
• Privacy – All votes must be secret.
• Unreusability – No voter can vote twice.
• Eligibility – No one who is not allowed to vote can vote.
• Fairness – Nothing must affect the voting. No one can indicate the tally before the votes are counted.
• Verifiability – No one can falsify the result of the voting.
• Robustness – The result reflects all submitted and well-formed ballots correctly, even if some voters and (or) possibly some of the entities running the election cheat.
• Uncoercibility – No voter should be able to convince any other participant of the value of its vote.
• Receipt-freeness – Voters must neither obtain nor be able to construct a receipt proving the content of their vote.
• Mobility – The voter can vote anytime and anywhere through internet.
• Convenience – System must allow voters to cast their votes quickly, in one session and with minimal equipment or special skills.
In the recent years, researchers are more focusing on developing a new technology which can support uncoercibility, receipt-freeness and also universal-verifiability. Many end-to-end verifiable systems (E2E) are proposed and being widely used. In principle, E2E voting system offer assurance to the voters as they cast their vote by distributing a receipt of their vote which can be used for verification purpose from the overall tabulation of the collected votes. Yet on the other hand, this receipt cannot be used as a proof in vote buying or vote coercion although all of the receipts will be posted publicly in a secured append-only Bulletin Board once the voter finished the voting process. Therefore, the E2E system would still protect the voter’s privacy.
This scheme was introduced by Naor and Shamir. In cryptography field, visual cryptography offers less computational performance compare to the other cryptography schemes due to their complex cryptographic algorithms used to protect a secret. It encrypts visual information, for example pictures, text, etc. in a particular way and produces a set of shares as the result. These shares need to be stacked altogether by using a visual cryptography tool to reveal the hidden secret .Visual Cryptography is a method for protecting image-based secrets that has a computation-free decryption process .
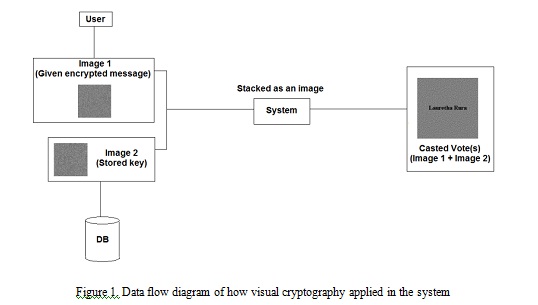
Figure 1. Data flow diagram of how visual cryptography applied in the system
It can be considered as a convenient and reliable tool for secret protection or even for verification (authentication) process because it is not time-consuming, low in computational cost and could still be done without any external devices needed. Illustration on how visual cryptography works in electronic voting system is displayed in Fig. 1. Image Steganography
Steganography is the art of hiding information in ways that prevent the detection of hidden messages [12]. It is introduced as a branch of information security based on the needs of providing an enhanced security technique of hiding secret information. As the information technology evolves, more threats arise and a simple encryption method is just not sufficient enough to protect the secrecy of data anymore. An encrypted data could easily cause suspicion since it is clearly shown as one. On the other hand, steganography offers a less suspicious way of hiding a secret. Therefore, steganography is proposed to be used as a main tool in this paper to secure the data communication in the election procedure, as its purpose is to maintain a secret communication between two parties. This scheme could be applied to various types of data such as text, images, audio, video and protocol file format. The methods of steganography vary from invisible inks, microdots, character arrangement, digital signatures, covert channels, to spreadspectrum communications.
Unlike cryptography, the input and output data (stego-object) of steganography would be identical. As a result, it would be difficult to recognize and interpret the hidden secret in the stego-object. However some of the steganography schemes like text steganography are limited in data encoding. Thus, they are not completely feasible to be applied in the system. Image steganography on the other hand, give a better encoding technique to be used as it can securely hide the secret message. It supports data transmission process by securely transferring a hidden secret in a digital image file. For this reason, image steganography would be applied in this system together with secret-ballot receipts scheme and visual cryptography in the voting stage and also to be used throughout the system for data transmission process.
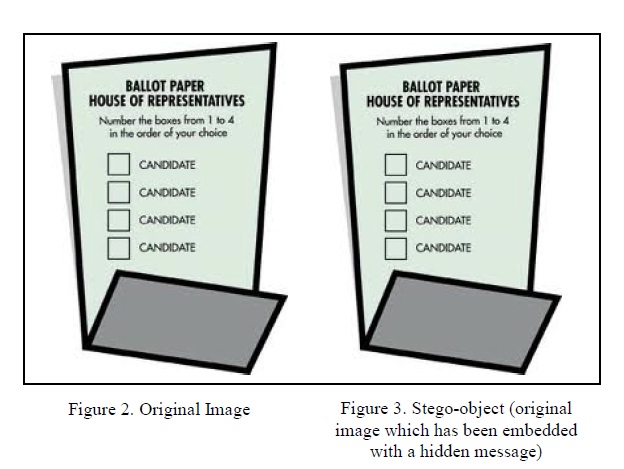
Fig. 2 and Fig. 3 shows the comparison of an original and stego-image with very unnoticeable difference. Fig. 2 is the original image and Fig. 3 has been encoded with random encrypted words. Image steganography can be separated into two types based on its compression method, image (spatial) domain and transform (frequency) domain [13]. For image domain, a message would directly be embedded into a source image and then it would be compressed with lossy compression. Therefore, all the embedded information would not be altered in the compression phase. On the other hand, in transform domain, message would be embedded into an image in between the compression phases with both lossy and lossless compression. In general, transform domain is more robust compare to image domain technique because it eliminates the possibility of message being destroyed during the compression process when the excess image data is removed (lossy compression).
The principle of secret-ballot receipt lays in the concept where privacy violation should not occur at all in the election, to ensure its integrity and also to prevent altered votes in the election process due to vote buying or selling and vote coercion [8], [14]. The technique provides a direct assurance of each voter’s vote. The implementation of secret–ballot receipts scheme helps to reduce the need for physical security, audit and observation in several stages of the system as it does not require any external hardware to be applied as a compliment to its functionality. The initial flow of secret ballot receipts implementation requires each voter to use an external hardware (printer) in order to retrieve and verify their casted ballots in a printed receipt.
It also applies the same concept as Naor and Shamir in visual cryptography [9], where a secret – in this case, a vote that is hidden in two separated layer of pixel symbols. The secret would only be revealed once those layers are overlaying one another. However, to minimize external hardware usage in the election process, instead of generating a printed receipt, the system would then generate a digital receipt in an image format to each voter. Chaum also proposed the conjunction of mix-net scheme in the secret-ballot receipt to ensure the integrity and privacy of the tallying process [8].
Here, the voter’s chosen layer would be passed respectively among few trustees who are going to generate intermediate batches based on voter’s receipt batch as an input. The final product of this process is a tally batch in the form of ballot image. However, the processes would be time-consuming because different trustees (servers) are required to be included in the election procedure. Hence, a simple amendment made to the applied mix-net scheme would be introduced in this paper in order to fulfill the system’s requirement by implementing threshold decryption scheme.
1. H. Wei, Z. Dong, C. Ke-fei, "A receipt-free punch-hole ballot electronic voting scheme," Signal-Image Technologies and Internet-Based System, 2007. SITIS 2007. Third International IEEE Conference, pp.355-360, Shanghai Jiaotong University, China, Dec. 16-18, 2007
2. L. Langer, A. Schmidt, R. Araujo, “A pervasively verifiable online voting scheme,” Informatik 2008 LNI, vol. 133, pp. 457-462, 2008
3. www. ieeexplore.ieee.org
| Are you interested in this topic.Then mail to us immediately to get the full report.
email :- contactv2@gmail.com |