




Published on Nov 30, 2023
In recent years, the emergence of mobile phones has made their appearance in the cyberspace. These smart phones can be used for normal telephonic purposes like making a call or sending text messages etc, and advanced purposes like checking e-mails, chatting online using any IMs, playing games with interactive GUIs, cloud services, etc. Thus security plays a vital role in today’s mobile world.
In this project, a method is proposed to overcome certain disadvantages faced by symmetric algorithms during key exchange in the internet using a simple call blocker application that synchronizes user data with the user’s account in the server. There are security issues like sniffing of data while accessing information through open channel. Proper security measures can help to deal with the common security threats faced by mobile phone users such as data protection, privacy, application and personal information security.
Cryptographic techniques play an important role in protecting communication links and data, since access to data can be limited to those who hold the proper key. This project discusses a method to securely access information in a network by an android mobile application using AES cryptographic technique. The project also describes a new key sharing algorithm, based on symmetric key management for faster and efficient encryption of data that is suitable for use in a mobile device.
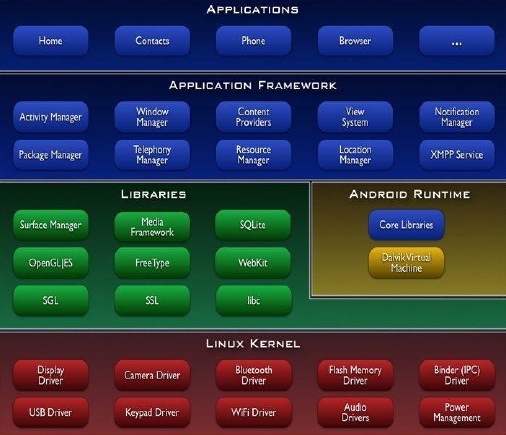
The rapid growth of portable electronic devices with limited power and memory has opened a vast area of mobile computing and challenges for implementing security in such devices which are always connected to the internet. Smart phones that are powered by either Android OS, iOS, Web OS, Bada OS, BlackBerry OS or Windows Phone OS are examples of portable electronic devices that are becoming an integral part of everyday life. Android is a software stack for mobile devices that includes an operating system, middleware and key applications.
The Android SDK provides the tools and APIs necessary to develop applications on the Android platform using the Java programming language. The main building blocks of Android platform are device hardware, operating system and application runtime. The Android application sandbox isolates data and code execution on a per-application basis. Android application frameworks use robust implementations of common security functionality such as cryptography, permissions and secure IPC.
• Application framework – enabling reuse and replacement of components Dalvik virtual machine – optimized for mobile devices
• Integrated browser – based on the open source WebKit engine
• Optimized graphics – powered by a custom 2D graphics library; 3D graphics based on the OpenGL ES 1.0 specification (hardware acceleration optional)
• SQLite – for structured data storage
• Media support – for common audio, video and still image formats (MPEG4, H.264, MP3, AAC, AMR, JPG, PNG, GIF)
• GSM Telephony – hardware dependent
• Bluetooth, 3G, EDGE, WiFi – hardware dependent
• Camera, GPS, compass and accelerometer – hardware dependent
• Rich development environment – including a device emulator, tools for debugging, memory and performance profiling, and a plug-in for the Eclipse IDE
Fig 1.1 represents the Android system architecture.
Security is very important aspect of computer systems. In our daily life we use computer systems because we believe that the systems are secure. Cryptography is what makes the computer systems secure. Cryptography is a branch of mathematics science. The first publications about cryptography were published long time ago and are almost as old as first mathematical publication.
The first known cipher called Caesar cipher was used by Julius Caesar who lived 50 years before Christ (50 B.C.), but according to Menezes, van Oorschot, Vanstone (2001) limited cryptography has been used by Egyptians 4000 years ago. Since that time cryptography, mainly driven by military demand, became much more robust and in the 20th century, where first cipher machines were introduced during Second World War and later when computers and asymmetric algorithms came into play cryptography has become topic of many publications every year.
Many encryption algorithms are widely available and used in information security. They can be categorized into symmetric (private) and asymmetric (public) key encryption. In Symmetric keys encryption or secret key encryption, only one key is used to encrypt and decrypt data. The key should be distributed before transmission between entities. Key plays an important role. If weak key is used in algorithm then everyone may decrypt the data. Strength of Symmetric key encryption depends on the size of key used. For the same algorithm, encryption using longer key is harder to break than the one done using smaller key. Some examples of such algorithms are RC2, DES, 3DES, AES, etc.
Asymmetric key encryption or public key encryption is used to solve the problem of key distribution. In Asymmetric keys, two keys are used; private and public keys. Public key is used for encryption and private key is used for decryption (E.g. RSA and Digital Signatures). Because users tend to use two key: public key, which is known to public and private key which is known only to the user. There is no need for distributing them prior to transmission. However, public key encryption is based on mathematical functions, computationally intensive.
This project involves design of a secure call blocker application which employs AES technique. The traditional non – secure data communications are eliminated in this approach. In addition to the call blocking facility, the blacklists of every user is stored securely in online server totally free of cost. Irrespective of the received call phone numbers, the application works by blocking unwanted calls. The result from our performance analysis suggests that AES symmetric encryption along with the newly implemented key sharing algorithm is a better secure method than the available RSA and ECC techniques. Since the users’ blacklisted are stored on the online server, it can also be accessed by the web client page where the user can modify the blacklist and the changes are retrieved automatically by the mobile client.
The hardware and software requirements for the development phase of our project are:
• OS: Windows 7 (64 bit) or any Linux distro (64 bit)
• Android OS: Froyo v2.2 (minimum)
• Database: SQLite for Android
• WAMP for testing the web server locally
• Mobile Processor: ARM 11 @ 528 MHz (minimum)
• Notebook Processor: Intel Core i5-2410M @ 2.30 GHz
• Data connectivity: WiFi or 3G
• Web server: Any web server or cloud that is hosted online in the internet and is up all the time